반응형
OpenLDAP 그룹 및 계정 생성
정보 확인
$ docker exec openldap ldapsearch -x -b dc=4wxyz,dc=com \
-D "cn=admin,dc=4wxyz,dc=com" \
-w ldappassword
--output--
# extended LDIF
#
# LDAPv3
# base <dc=4wxyz,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# 4wxyz.com
dn: dc=4wxyz,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: 4wxyz
dc: 4wxyz
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
$ docker exec openldap slapcat
--output--
dn: dc=4wxyz,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: 4wxyz
dc: 4wxyz
structuralObjectClass: organization
entryUUID: a8f0a940-6072-103b-9813-9597cb19f842
creatorsName: cn=admin,dc=4wxyz,dc=com
createTimestamp: 20210613090827Z
entryCSN: 20210613090827.781013Z#000000#000#000000
modifiersName: cn=admin,dc=4wxyz,dc=com
modifyTimestamp: 20210613090827Z
$ docker exec openldap slaptest
--output--
config file testing succeededorganizationalRole admin
$ vim oR-admin.ldif
dn: cn=admin,dc=4wxyz,dc=com
cn: admin
roleOccupant: dc=4wxyz,dc=com
objectClass: organizationalRole
objectClass: top
description: LDAP Manager$ docker exec openldap ldapadd -x -D cn=admin,dc=4wxyz,dc=com \
-w ldappassword \
-f /container/service/slapd/assets/custome/oR-admin.ldif \
-ZZ
--output--
adding new entry "cn=admin,dc=4wxyz,dc=com"
organizationalUnit Groups, People 생성
$ vim oU-groups.ldif
# Groups, 4wxyz.com
dn: ou=Groups,dc=4wxyz,dc=com
ou: Groups
objectClass: organizationalUnit
objectClass: top
# People, 4wxyz.com
dn: ou=People,dc=4wxyz,dc=com
ou: People
objectClass: organizationalUnit
objectClass: top$ docker exec openldap ldapadd -x -D cn=admin,dc=4wxyz,dc=com \
-w ldappassword \
-f /container/service/slapd/assets/custome/oU-groups.ldif \
-ZZ
--output--
adding new entry "ou=Groups,dc=4wxyz,dc=com"
adding new entry "ou=People,dc=4wxyz,dc=com"posixGroup infra,dev 생성
$ vim groups.ldif
# admin, Groups, 4wxyz.com
dn: cn=admin,ou=Groups,dc=4wxyz,dc=com
cn: admin
objectClass: posixGroup
objectClass: top
gidNumber: 1200
description: Administrator Team
#memberUid: 1201
# secu, Groups, 4wxyz.com
dn: cn=secu,ou=Groups,dc=4wxyz,dc=com
cn: secu
objectClass: posixGroup
objectClass: top
gidNumber: 1300
description: Security Team
#memberUid: 1301
# infra, Groups, 4wxyz.com
dn: cn=infra,ou=Groups,dc=4wxyz,dc=com
cn: infra
objectClass: posixGroup
objectClass: top
gidNumber: 1500
description: Infrastructure Team
#memberUid: 1501
# dev, Groups, 4wxyz.com
dn: cn=dev,ou=Groups,dc=4wxyz,dc=com
cn: dev
objectClass: posixGroup
objectClass: top
gidNumber: 1600
description: Development Team
#memberUid: 1601
# plan, Groups, 4wxyz.com
dn: cn=plan,ou=Groups,dc=4wxyz,dc=com
cn: plan
objectClass: posixGroup
objectClass: top
gidNumber: 1700
description: Planning Team
#memberUid: 1701
# design, Groups, 4wxyz.com
dn: cn=design,ou=Groups,dc=4wxyz,dc=com
cn: design
objectClass: posixGroup
objectClass: top
gidNumber: 1800
description: Design Team
#memberUid: 1801
# publisher, Groups, 4wxyz.com
dn: cn=publisher,ou=Groups,dc=4wxyz,dc=com
cn: publisher
objectClass: posixGroup
objectClass: top
gidNumber: 1900
description: Publisher Team
#memberUid: 1901$ docker exec openldap ldapadd -x -D cn=admin,dc=4wxyz,dc=com \
-w ldappassword \
-f /container/service/slapd/assets/custome/groups.ldif \
-ZZ
--output--
adding new entry "cn=admin,ou=Groups,dc=4wxyz,dc=com"
adding new entry "cn=secu,ou=Groups,dc=4wxyz,dc=com"
adding new entry "cn=infra,ou=Groups,dc=4wxyz,dc=com"
adding new entry "cn=dev,ou=Groups,dc=4wxyz,dc=com"
adding new entry "cn=plan,ou=Groups,dc=4wxyz,dc=com"
adding new entry "cn=design,ou=Groups,dc=4wxyz,dc=com"
adding new entry "cn=publisher,ou=Groups,dc=4wxyz,dc=com"posixAccount testuser1 생성
$ vim new-user.ldif
dn: uid=testuser1,ou=People,dc=4wxyz,dc=com
uid: testuser1
cn: testuser1
sn: 3
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: posixAccount
objectClass: inetOrgPerson
objectClass: shadowAccount
loginShell: /bin/bash
homeDirectory: /home/testuser1
uidNumber: 1501
gidNumber: 1500
userPassword: {SSHA}j3lBh1Seqe4rqF1+NuWmjhvtAni1JC5A
mail: testuser1@4wxyz.com
gecos: testuser1 User$ docker exec openldap ldapadd -x -D cn=admin,dc=4wxyz,dc=com \
-w ldappassword \
-f /container/service/slapd/assets/custome/new-user.ldif \
-ZZ
--output--
adding new entry "uid=testuser1,ou=People,dc=4wxyz,dc=com"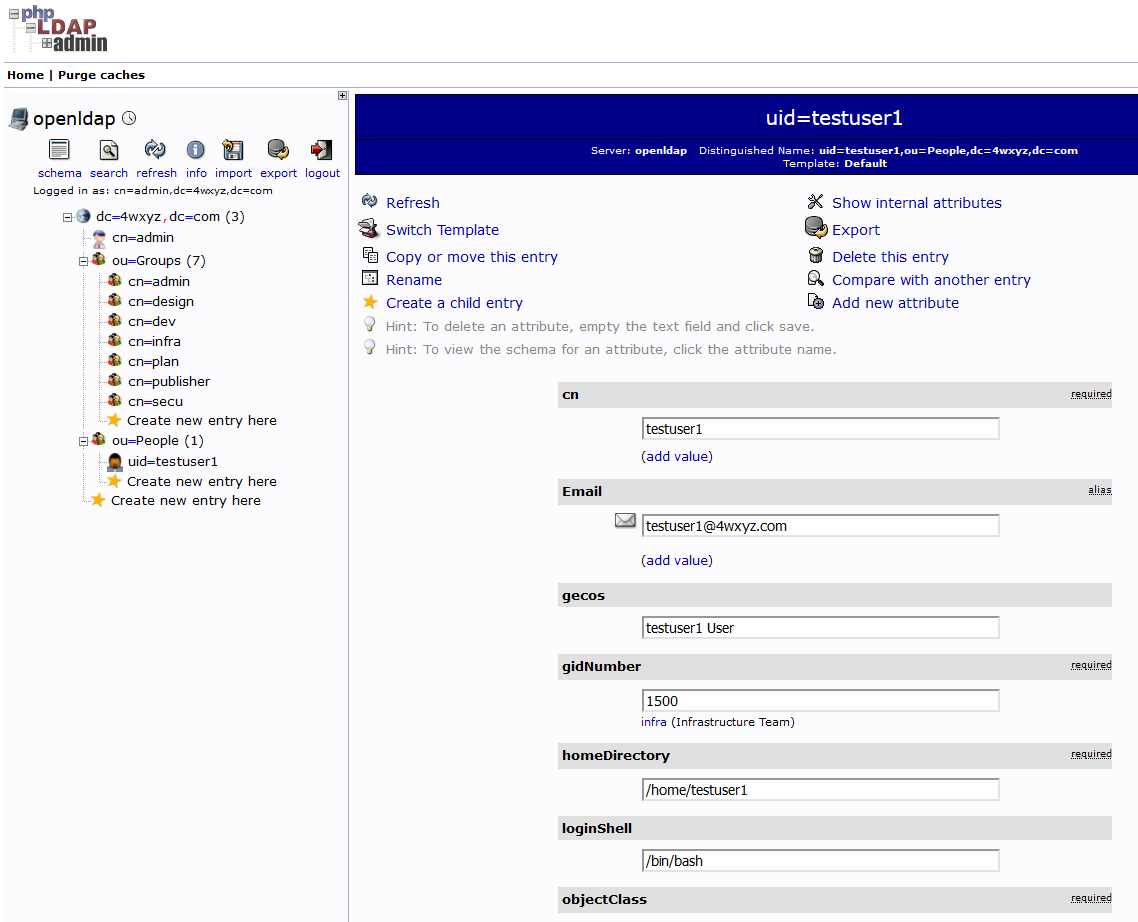
기본 계정 생성
$ docker exec openldap cp container/service/slapd/assets/test/new-user.ldif \
container/service/slapd/assets/custome/new-user.ldif
$ docker exec openldap ldapadd -x -D "cn=admin,dc=4wxyz,dc=com" \
-w ldappassword \
-f /container/service/slapd/assets/custome/testuser.ldif -ZZ
$ docker exec openldap ldappasswd -s password \
-w ldappassword \
-D "cn=admin,dc=4wxyz,dc=com" \
-x "uid=testuser,dc=4wxyz,dc=com"
$ docker exec openldap ldapsearch -x -b "uid=testuser,dc=4wxyz,dc=com" \
-D "cn=admin,dc=4wxyz,dc=com" \
-w ldappasswordLDAP 클라이언트 설정
LDAP enable
$ authconfig --enableldap \
--enableshadow \
--enableldapauth \
--enablelocauthorize \
--disableldaptls \
--ldapserver=192.168.56.101 \
--ldapbasedn="dc=4wxyz,dc=com" \
--disablecache \
--enablemkhomedir \
--updateLDAP 계정 조회
$ getent passwdLDAP disable
$ authconfig --disableldap --disableldapauth --update
728x90
반응형
'리눅스' 카테고리의 다른 글
| [LDAP] OpenLDAP 스크립트로 그룹 생성 및 사용자 계정 (0) | 2021.06.13 |
|---|---|
| [LDAP] OpenLDAP Password Policy overlay (ppolicy) (0) | 2021.06.13 |
| [LDAP] OpenLDAP 설치 및 구성 (0) | 2021.06.11 |
| 도커 컴포즈 설치(docker-compose install) (0) | 2021.06.10 |
| chage 명령어 (0) | 2021.06.09 |



