HashiCorp Vault SSH Client-Signer Secrets Engine을 통한 SSH 인증 구성 방법
Vault 서버에서 SSH 인증을 위한 CA(Certificate Authority) 역할을 수행하게 하며 각 SSH 서버와 클라이언트는 Vault에서 생성된 CA를 신뢰하도록 설정됩니다.
테스트 환경
| 호스트 이름 | 아이피 | 역할 | 운영체제 | 비고 |
| node1 | 192.168.10.111 | vault server | ubuntu 22.04 | |
| node2 | 192.168.10.112 | ssh server | ubuntu 22.04 | |
| node3 | 192.168.10.113 | ssh client | ubuntu 22.04 |
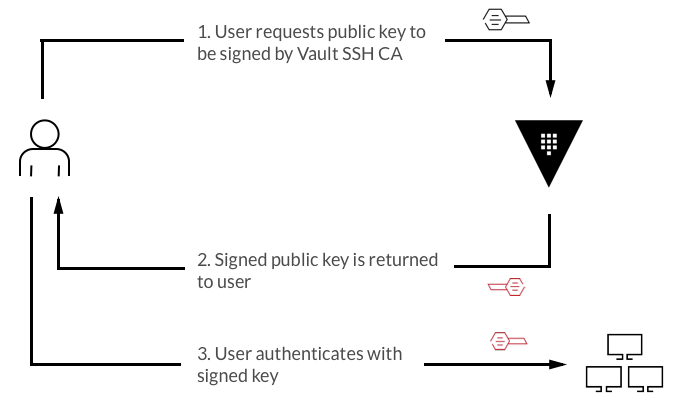
1. Vault 데이터 디렉터리 초기화 및 서버 재시작
sudo systemctl stop vault
sudo rm -rf /opt/vaultsudo mkdir -pv /opt/vault/data
sudo chown -R vault:vault /opt/vault
sudo systemctl start vault
sudo systemctl status vault2. Vault 설치
GPG 키와 저장소 추가
wget -O- https://apt.releases.hashicorp.com/gpg \
| sudo gpg --dearmor --yes -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" \
| sudo tee /etc/apt/sources.list.d/hashicorp.listVault 설치
sudo apt update
sudo apt install -y vault
vault versionVault 설정 파일 구성
sudo tee /etc/vault.d/vault.hcl > /dev/null <<EOF
ui = true
storage "file" {
path = "/opt/vault/data"
}
# HTTP listener
listener "tcp" {
address = "0.0.0.0:8200"
tls_disable = 1
}
EOFVault 서비스 시작 및 확인
sudo systemctl enable --now vault
sudo systemctl restart vault
sudo systemctl status vaultVault 서비스 로그 확인
sudo journalctl -xeu vault
sudo journalctl -u vault -b3. Vault 서버 환경 변수 설정
Vault 서버의 주소를 환경 변수로 설정하여 사용자가 Vault CLI를 통해 손쉽게 서버와 상호작용할 수 있도록 합니다.
echo "export VAULT_API_ADDR=http://127.0.0.1:8200" >> ~/.bashrcecho "export VAULT_ADDR=http://127.0.0.1:8200" >> ~/.bashrcsource ~/.bashrc4. Vault 초기화 및 언실
vault statusKey Value
--- -----
Seal Type shamir
Initialized false
Sealed true
Total Shares 0
Threshold 0
Unseal Progress 0/0
Unseal Nonce n/a
Version 1.18.1
Build Date 2024-10-29T14:21:31Z
Storage Type file
HA Enabled falseVault 초기화(Initialize Vault)
vault operator init -key-shares=1 -key-threshold=1 | tee vault-init-$(date +"%Y%m%d-%H%M%S").txtVault UI 접속
http://192.168.10.111:8200unseal 및 로그인
vault operator unseal {Unseal Key}
vault operator unseal QttKV0C6S/xPLrPRqIAC5p+Dx10GhOX+MADzz4U0r7M=vault login {Initial Root Token}
vault login hvs.fZozwuLaIBEsH7SNsmtsR9w1Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token hvs.fZozwuLaIBEsH7SNsmtsR9w1
token_accessor TSXjJXZAJkgsVp24csou7JWH
token_duration ∞
token_renewable false
token_policies ["root"]
identity_policies []
policies ["root"]토큰(token)에 대한 정보 표시
vault token lookupKey Value
--- -----
accessor TSXjJXZAJkgsVp24csou7JWH
creation_time 1731497524
creation_ttl 0s
display_name root
entity_id n/a
expire_time <nil>
explicit_max_ttl 0s
id hvs.fZozwuLaIBEsH7SNsmtsR9w1
meta <nil>
num_uses 0
orphan true
path auth/token/root
policies [root]
ttl 0s
type serviceseal 및 HA 상태 출력
vault statusKey Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.18.1
Build Date 2024-10-29T14:21:31Z
Storage Type file
Cluster Name vault-cluster-1adb0469
Cluster ID 588a0f37-9dba-8b31-8f9a-51826d788a25
HA Enabled false5. Syslog를 통한 Vault Audit 로깅 활성화
vault audit enable syslogSuccess! Enabled the syslog audit device at: syslog/6. SSH Client-Signer Secrets Engine 활성화 및 CA 키 생성
SSH Client-Signer Secrets Engine을 활성화하여 Vault가 SSH 키 서명 기능을 수행할 수 있도록 합니다.
vault secrets enable -path=ssh-client-signer sshSuccess! Enabled the ssh secrets engine at: ssh-client-signer/클라이언트 CA(인증 기관) 인증서 생성
vault write ssh-client-signer/config/ca generate_signing_key=trueKey Value
--- -----
public_key ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDXqZnO1TlCMKo8STV9yFi4PLMAed96vvL49/5UP26xcGE38/v9k5MAgE+bkszLdOIWL5vShOdiARpi+oOoI1zSXy/p2nBtlfU58RnSADWf44YNYlgfyjKWmO9HtT7p4sFRneCCHX/i74En/leniH40XifEpqzNWUaFD8MyWGFLVqeHtgnVFIsLGTS4iazfISLcSP/9jtCWTrpqFIaIrYXRUgLDrUg4X/JuMFGOyDxTed+MEbN13TidID5Pys79L6FnjiyS8rwUHLpAFQbmc0SX3SxjRuFUPp2+AfybnfSzAIy1OXbclU/Estp2m7v+nhf71gY2Rx49PgYK1eKYFfNxj7faeY9aSSf/Hm++xo4YTyGLa6YrezY7SXn50EmBfbORxMZD/RSznRPyw0gvIx3R6sRyWInAwUEAmrx/ZEV/H0aweeLwSt8QfS7WjM/G03QPZ11EqygyzHLgFpCgqnvoAMq9jR7rXhiPl/FrZRTHqlKgnZ8dnwbiyPhKI/Xz5ZyU7bJFvk3Za7Us+xm38WKi2E5Q52hCDgOcK37OX18IEH5mkbEvlFLCpLcw7P4HdD9KvjOBDSMCi0rgwuULyRsb4tJWhpgvLozO8J5xAGuT5Jzs1P4R/SRgnwZOX2PDrgXrfByo3ZYAm5+GlR9mXMbhpo0D1TyfO2EB+ZXWEoEKqw==CA 공개 키 출력
vault read -field=public_key ssh-client-signer/config/ca > /etc/ssh/trusted-user-ca-keys.pem$ cat /etc/ssh/trusted-user-ca-keys.pem
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDXqZnO1TlCMKo8STV9yFi4PLMAed96vvL49/5UP26xcGE38/v9k5MAgE+bkszLdOIWL5vShOdiARpi+oOoI1zSXy/p2nBtlfU58RnSADWf44YNYlgfyjKWmO9HtT7p4sFRneCCHX/i74En/leniH40XifEpqzNWUaFD8MyWGFLVqeHtgnVFIsLGTS4iazfISLcSP/9jtCWTrpqFIaIrYXRUgLDrUg4X/JuMFGOyDxTed+MEbN13TidID5Pys79L6FnjiyS8rwUHLpAFQbmc0SX3SxjRuFUPp2+AfybnfSzAIy1OXbclU/Estp2m7v+nhf71gY2Rx49PgYK1eKYFfNxj7faeY9aSSf/Hm++xo4YTyGLa6YrezY7SXn50EmBfbORxMZD/RSznRPyw0gvIx3R6sRyWInAwUEAmrx/ZEV/H0aweeLwSt8QfS7WjM/G03QPZ11EqygyzHLgFpCgqnvoAMq9jR7rXhiPl/FrZRTHqlKgnZ8dnwbiyPhKI/Xz5ZyU7bJFvk3Za7Us+xm38WKi2E5Q52hCDgOcK37OX18IEH5mkbEvlFLCpLcw7P4HdD9KvjOBDSMCi0rgwuULyRsb4tJWhpgvLozO8J5xAGuT5Jzs1P4R/SRgnwZOX2PDrgXrfByo3ZYAm5+GlR9mXMbhpo0D1TyfO2EB+ZXWEoEKqw==7. SSH 인증 역할 설정
서명된 인증서를 통해 인증 가능한 사용자를 제한하고 기본 사용자 및 인증서 TTL(Time To Live)을 설정합니다.
vault write ssh-client-signer/roles/my-role -<<"EOH"
{
"allow_user_certificates": true,
"allowed_users": "*",
"valid_principals": "vagrant",
"default_extensions": [
{
"permit-pty": ""
}
],
"key_type": "ca",
"default_user": "vagrant",
"ttl": "30m0s"
}
EOHSuccess! Data written to: ssh-client-signer/roles/my-rolerole 정보 확인
vault read ssh-client-signer/roles/my-roleKey Value
--- -----
algorithm_signer default
allow_bare_domains false
allow_host_certificates false
allow_subdomains false
allow_user_certificates true
allow_user_key_ids false
allowed_critical_options n/a
allowed_domains n/a
allowed_domains_template false
allowed_extensions n/a
allowed_user_key_lengths map[]
allowed_users *
allowed_users_template false
default_critical_options map[]
default_extensions map[permit-pty:]
default_extensions_template false
default_user vagrant
default_user_template false
key_id_format n/a
key_type ca
max_ttl 0s
not_before_duration 30s
ttl 30m8. SSH 서버 설정 (CA 키 설정)
Vault에서 생성한 CA 키를 SSH 서버에서 신뢰하도록 설정합니다.
ssh(sshd) server 작업
trusted-user-ca-keys.pem(/etc/ssh/trusted-user-ca-keys.pem) 저장
curl -s http://192.168.10.111:8200/v1/ssh-client-signer/public_key -o /etc/ssh/trusted-user-ca-keys.pemcat /etc/ssh/trusted-user-ca-keys.pemssh(sshd) 설정(/etc/ssh/sshd_config)
echo 'TrustedUserCAKeys /etc/ssh/trusted-user-ca-keys.pem' >> /etc/ssh/sshd_configecho "PubkeyAcceptedKeyTypes=+ssh-rsa,ssh-rsa-cert-v01@openssh.com" >> /etc/ssh/sshd_configssh(sshd) 설정 확인
cat /etc/ssh/sshd_config | egrep 'TrustedUserCAKeys|PubkeyAcceptedKeyTypes'ssh(sshd) 재기동
sshd -tsystemctl restart sshd9. 클라이언트 측 SSH 키 생성 및 서명
클라이언트에서 SSH 키를 생성하고 Vault에서 서명된 인증서를 생성하여 SSH 접속에 사용합니다.
SSH 키 생성
ssh-keygen -t rsa -C "vagrant@vault" -f ~/.ssh/id_rsa
echo 'export VAULT_ADDR=http://192.168.0.51:8200' >> ~/.bashrcecho 'export VAULT_TOKEN="hvs.fZozwuLaIBEsH7SNsmtsR9w1"' >> ~/.bashrcsource ~/.bashrcenv | grep VAULTVault에서 SSH 키 서명 요청
vault write -field=signed_key ssh-client-signer/sign/my-role public_key=@$HOME/.ssh/id_rsa.pub > ~/.ssh/signed-cert.pub서명된 인증서 확인
ssh-keygen -Lf ~/.ssh/signed-cert.pub10. SSH 서버로 접속
서명된 인증서를 사용하여 SSH 서버에 접속합니다.
ssh -i ~/.ssh/signed-cert.pub -i ~/.ssh/id_rsa vagrant@192.168.10.112
참고URL
- HashiCorp Vault를 이용한 SSH 공개키 인증 : https://ikcoo.tistory.com/251
- Signed SSH Certificates : https://developer.hashicorp.com/vault/docs/secrets/ssh/signed-ssh-certificates
- client key signing : https://developer.hashicorp.com/vault/docs/secrets/ssh/signed-ssh-certificates#client-key-signing
- host key signing : https://developer.hashicorp.com/vault/docs/secrets/ssh/signed-ssh-certificates#host-key-signing
- 複雑なポリシーを適切に管理する、HashiCorp Vault SSH CA動的シークレットエンジンとSentinel : https://www.lac.co.jp/lacwatch/service/20200811_002237.html
- Managing Developer Access with Vault SSH : https://pacewisdom.com/blog/managing-developer-access-with-vault-ssh/
'리눅스' 카테고리의 다른 글
| SSH 인증을 위한 SSH 인증서를 구성하고 설정하는 방법 (0) | 2023.01.20 |
|---|---|
| [리눅스] centos에 hashicorp vault를 설치하는 방법(installing vault) (0) | 2023.01.18 |
| [리눅스] 도커 컨테이너에 vault 설치하기(test) (0) | 2023.01.18 |
| HashiCorp Vault를 설치하고 설정하는 방법 (0) | 2023.01.18 |
| 우분투에 HashiCorp Vault를 설치하는 방법 (0) | 2023.01.18 |



